Smart-Home Automation
What Is Smart-Home Automation? Smart-home automation refers to using connected devices and software to control everyday household functions […]
What Is Smart-Home Automation? Smart-home automation refers to using connected devices and software to control everyday household functions […]
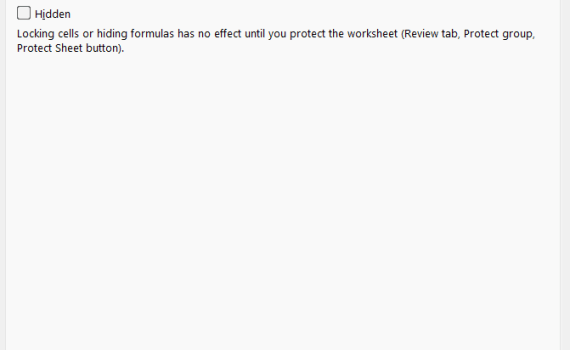
Do you have an Excel template for others to fill out and you want to make sure that […]
By going to the website virustotal.com, you can scan suspicious files and URLs to detect types of malware, […]
Are you trying to attach a database to SQL Server Management Studio and getting Error 5123? Are you […]
“On Sunday September 16 2018, engineers at Facebook detected some unusual activity on the social media platform’s networks. […]

This post discusses PDF security setting using the program Adobe Acrobat Pro 9. This post is the third […]
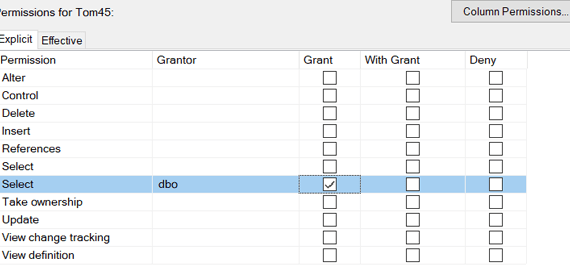
SQL Server security is a big topic. If you don’t know much about it then it will take […]

Public key cryptography (PKC) is an encryption technique that uses a paired public and private key (or asymmetric […]
What is cryptography? Wikipedia says: “Cryptography or cryptology is the practice and study of techniques for secure communication […]
Most government, large corporations, and even educational institutions want their users to change passwords after a certain time […]